NEWS
Microsoft 365 Security Tools - Part 1
- Details
- Written by Sara Oliveira
Microsoft 365 is a cloud-based productivity platform that includes apps like Microsoft Teams, Word, Excel, PowerPoint, Outlook, OneDrive, and more. Microsoft 365 also includes security and collaboration tools designed to make working internally and communicating with partners easier. Here are some tools offered in Microsoft 365 that can ensure the security of your company's information:
DLP
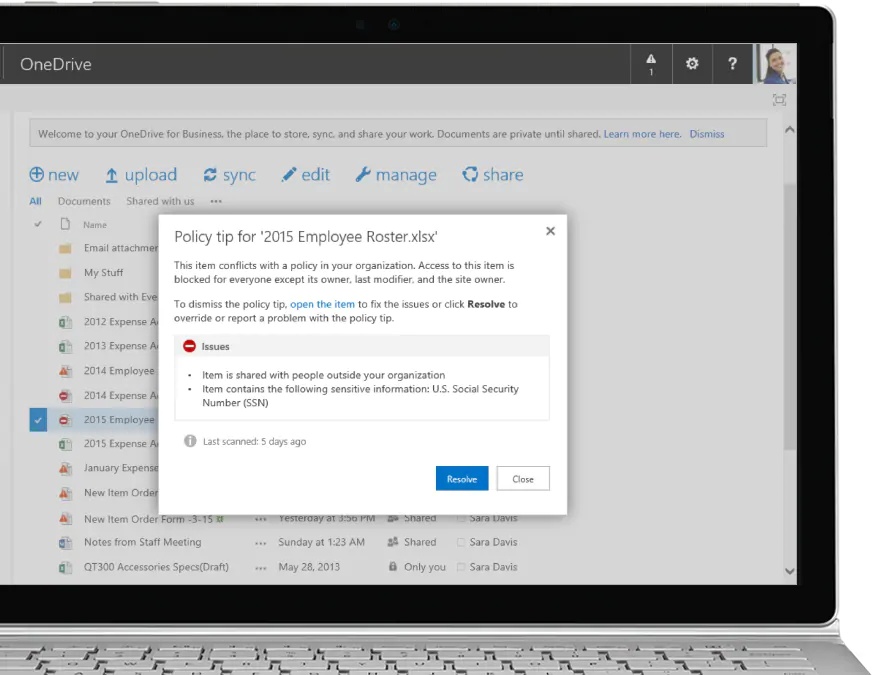
Data Loss Prevention Policies are policies designed to protect an organization's confidential information.
Based on conditions, DLPs ensure the protection of your information by alerting users or even preventing them from sharing confidential information with unauthorized persons.
Policies can work with Exchange Online, SharePoint Online, and OneDrive for Business, and are set in the Office 365 Security & Compliance Center, which is available in most Office 365 business plans.
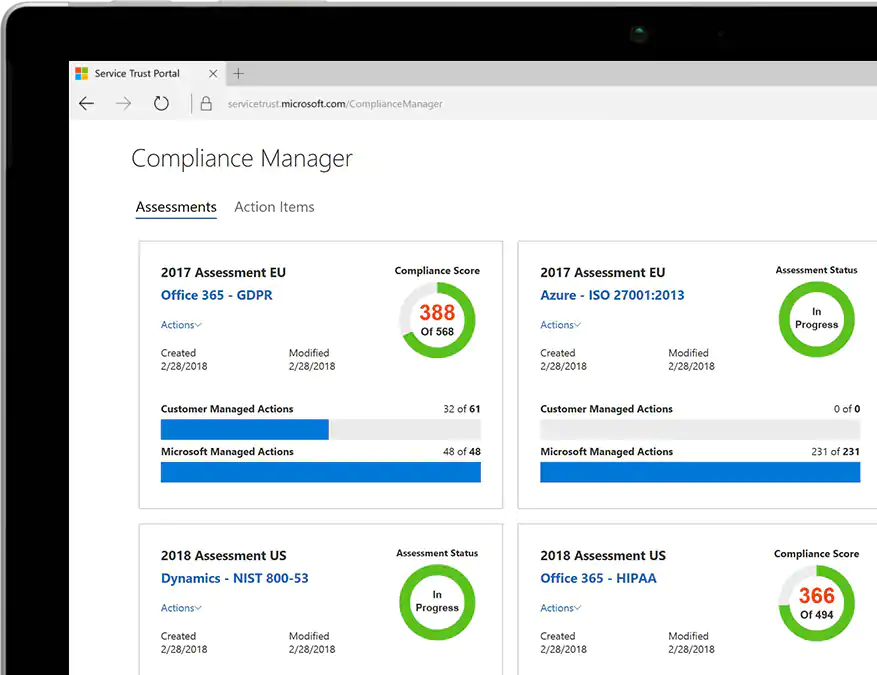
Secure Score
If your organization has a subscription that includes Office 365 Enterprise, Microsoft 365 Business, or Office 365 Business Premium, and you have the necessary permissions, you can view your organization's score by visiting https://securescore.office.com.
The secure scoring service discovers which Office 365 services you are using (for example, Exchange, SharePoint, and OneDrive), then analyzes your settings and activities and compares them to a baseline established by Microsoft. You will receive a score based on how aligned you are with security best practices.
You'll also get recommendations on steps you can take to improve your organization's score.
Using the secure scoring service helps increase the security of your organization by encouraging you to use the built-in security features of Office 365 (many of which you have purchased but may not be aware of).
- “The secure scoring service does not express an absolute measure of how likely your organization will have your data breached. It expresses the extent to which your organization has adopted controls that can reduce the risk of having your data breached. No service can guarantee that you will not be violated and the safe score should not be construed as a guarantee in any way. ”
- Hits: 870
ENCRYPTION VULNERABILITIES USING SHA-1
- Details
- Written by Caique Alves
SHA-1 is an encryption type with a cryptographic hash function. This means that with each encoding, a new hash is generated. This type of encoding method is also called a cryptographic hash function.
As already said, theoretically the SHA function should create a unique hash for all data inserted into it, but with increasing insertion, the chance of different peers creating the same hash number increases together, thus generating a collision between with these already generated numbers.
So with the collision, you can create an untrusted certificate with a hash identical to a trusted certificate. If they make you install this untrusted certificate, it can make a fake certificate as trusted and distribute malicious data.
The problem increased when attacks on the SHA-1 hash algorithm became more dangerous with “chosen prefix collision attacks”. It means collision attacks can now be performed with custom entries, and they are no longer just accidental, allowing malicious users to target files to duplicate and forge.

SHA-2 Usage
SHA-2 is a group of hashing algorithms that were created to replace SHA-1. SHA-2 contains several hash values, they are SHA-224, SHA-256, SHA-384 and SHA-512. SHA-256 is the default value.
There are a lot of different ways to create hashes, the algorithm used by SHA-2 is one of the most used for the balance between security and cost, it is a very efficient algorithm against collision attacks, the hashes combinations are much larger than the combinations of the SHA-1 type.
Another feature of the SHA-2 hash algorithm is that the size of the resulting hash is always the same, no matter how long it takes to generate, the result is always a sequence of 64 letters and numbers (with an encoding of 256 bits and 32 bytes).
SHA-2 has several uses and one of them is in Bitcoin, SHA-2 is used for the mining process, but also in the process of generating bitcoin addresses, this is due to the high level of security it offers.
Another important use is within the blockhain network, all nodes contain a 64-character hash copy representing the information, for example, an entire block. Once this information is validated by the network, any manipulation of this information by attempting to modify any character in the validated hash would be detected immediately and discarded.
Main difference SHA-1 e SHA-2
Hash values: SHA-1 generates a value of 160bits, SHA-2 generates 256 bits in the standard format.
Usage: SHA-1 used to sign SSL certificates, SHA-2 used as a function into blockchain.
Security: SHA-2 mais seguro pois contém 256 bits em seu formato padrão.
Diversity: SHA-2 contains 256 bits in its standard format, that’s why is more sucre than SHA-1.
- Hits: 798
OFFICE 2013 END OF SUPPORT
- Details
- Written by Sara Oliveira

Reduce your exposure to security risks by moving to a newer version of Office
After five years of Mainstream Support, and five years of Extended Support, Office 2013 will reach the End of Extended Support on April 11, 2023. Per the Fixed Lifecycle Policy, after this date security updates for Office 2013 will no longer be available. We recommend you upgrade to Microsoft 365 Apps, which includes the Office apps you are familiar with (such as Word, Excel, PowerPoint, and Outlook).
How this will affect your organization:
After Office 2013 reaches the end of support, Microsoft won’t provide any new security updates, and the continued use of Office 2013 after April 2023 may increase your organization’s exposure to security risks or impact your ability to meet compliance obligations.
Also, if you connect to Microsoft 365 with an Office 2013 client, you might experience performance or reliability issues. Since October 2020, Office 2013 is not a supported client to connect to Microsoft 365 services. These are the client versions of Office that are currently supported for connecting to Microsoft 365 (and Office 365) services (learn more):
- Microsoft 365 Apps
- Office LTSC 2021
- Office 2019
- Office 2016
What you need to do to prepare:
Please start upgrading to Microsoft 365 Apps, which is designed to receive regular updates, and will help you stay current by getting security updates and our latest features.
Alternatively, if your organization requires a static, unchanging product, consider moving to Office LTSC 2021. When evaluating your options, keep in mind the end of support dates for Office clients connecting to Microsoft 365 services (learn more).
- Hits: 2198
CAUTION WHEN COLLABORATING WITH EXTERNAL USERS ON MICROSOFT 365 TOOLS
- Details
- Written by Sara Oliveira

One of the great innovations brought by the Microsoft 365 suite is the power of team collaboration, in real time and completely online with co-workers on tasks, documents, chats, and whatever else you can imagine.
However, we often need to share information not only with co-workers, but with customers and suppliers, and OneDrive/SharePoint Online can be great tools for this, because its large storage capacities, as well as the intuitiveness of its use, make it very competitive with similar tools already on the market.
The point we often forget is that sharing and collaboration in these tools with external users (users outside your organizational domain) can be detrimental to the confidentiality of your company's information. You need to know what types of information employees can share with other users, as well as control so that information vital to your business is not sent or accessed by mistake by unauthorized users.
That's why it's very important to plan the implementation of tools like Microsoft Teams, OneDrive for Business and SharePoint Online so that you can work securely, maintaining collaboration between users.
It is necessary to consult an expert, who will assess your organization's scenario and indicate the best ways to work using these tools. For this, R2SIS Tecnologia has a team of professionals ready to help you.
- Hits: 2691
LIMIT ONEDRIVE AND SHAREPOINT ONLINE SESSION TIME
- Details
- Written by Sara Oliveira
We know that it is much more practical to keep passwords stored in internet browsers, not to block the computer session when we are away for short periods and keep active sessions in the browser, but often practicality is the enemy of security - even more so if we are dealing with confidential information.
Leaving data exposed on our computer screens while we are not present leaves the information vulnerable and accessible to users who are not authorized to access it. In the case of public or shared computers, the issue can be even worse, because if we forget an open session, another user who we don't even know can have access to our data.
As a solution to these issues, Microsoft provides the function to limit the session time of OneDrive for Business and SharePoint Online, so if the system detects inactivity for a period determined by the administrator, the user's session is automatically disconnected, and he/she will need enter his/her credentials again.
To learn how to protect your organization against unauthorized access to confidential information on OneDrive for Business and SharePoint Online, contact the R2SIS Tecnologia team of professionals.
- Hits: 1561

